
Security researchers from Reason Labs disclosed a critical vulnerability in the Facebook Messenger application for Windows that could allow attackers to hijack a call within the Messenger code to inject malware. The researchers also stated that it is a persistent threat that provides hackers undetected access to the application. The flaw was discovered in Facebook Messenger version 460.16, however, it is now fixed by the social media giant with the updated version 480.5 after Reason Labs reported the issue.
According to Reason Labs, the flaw initiates a call to load Windows Powershell from the C:\python27 path, which is generated while downloading version 2.7 of Python, and does not exist in most of the Windows installations. Cybercriminals can hijack these calls to stealthily execute malware without administrator knowledge.
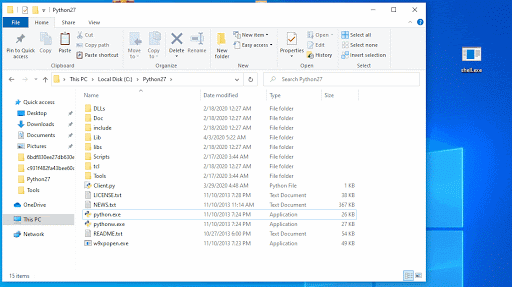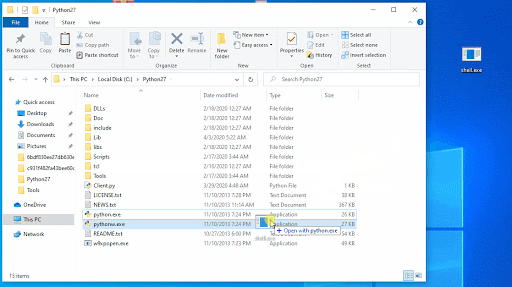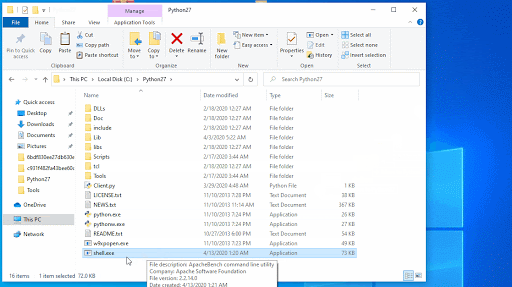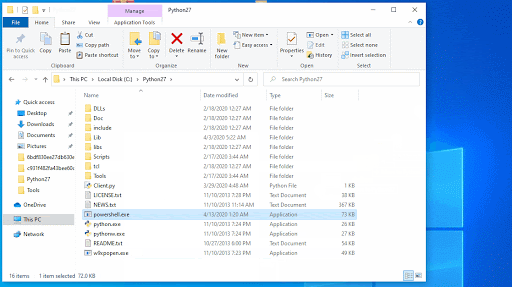
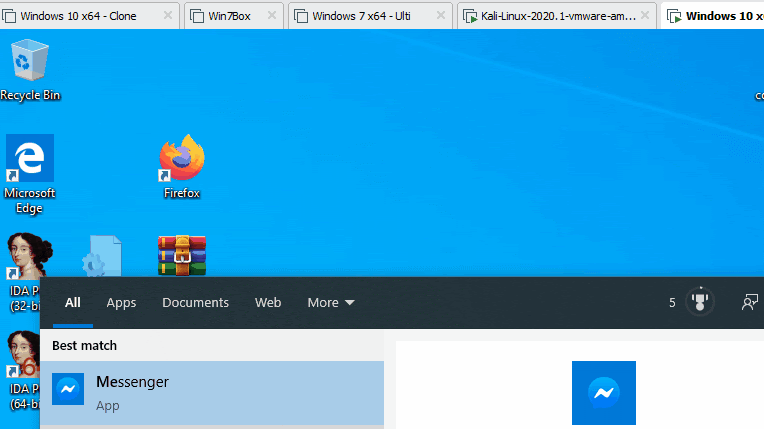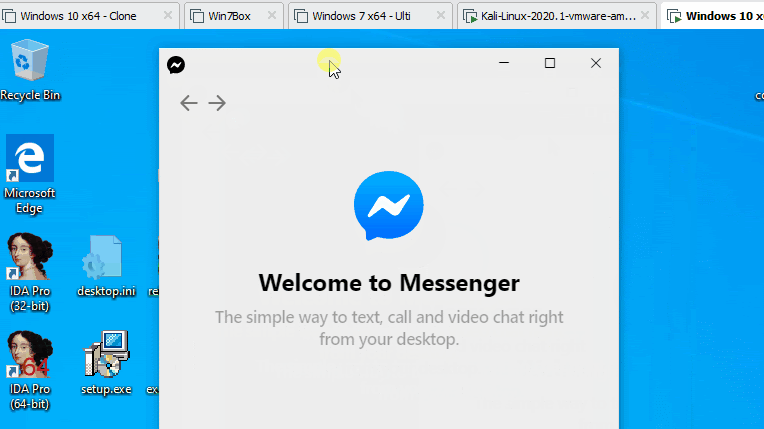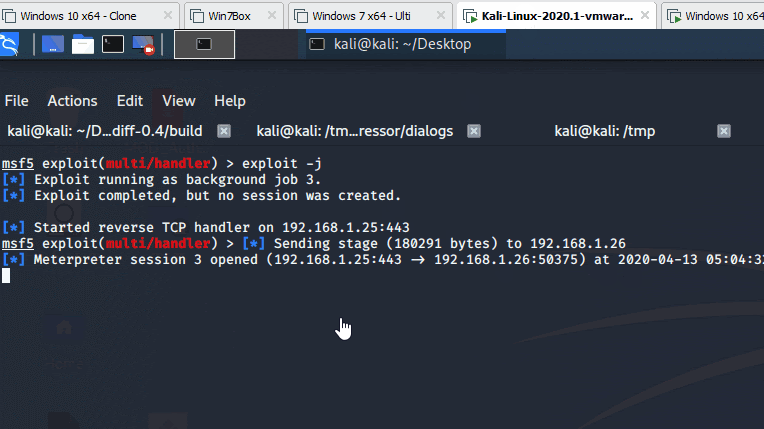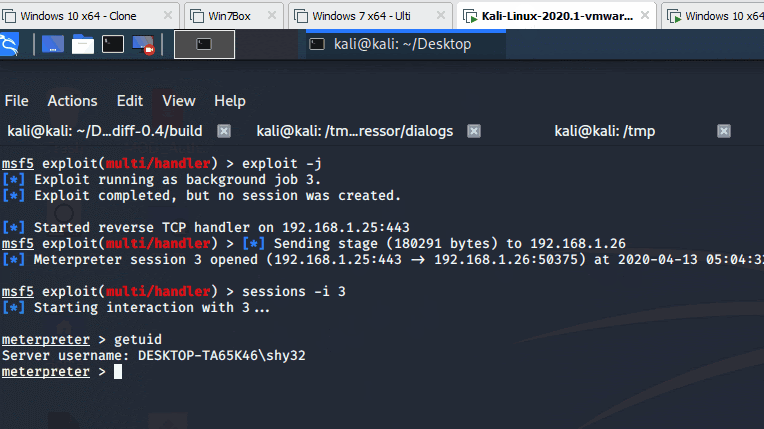
In order to test the bug, Reason Labs researchers created a reverse shell with msfvenom and a listener with Metasploit. The reverse shell was then renamed Powershell.exe and was installed into the Python directory (c:\python27). The researchers found that the vulnerable app triggered the call and executed the reverse shell, proving that potential attackers can abuse the flaw for persistent malware attacks.
It is better to be vigilant about the potential vulnerabilities in online applications for messaging and videoconferencing, and other remote working tools, as we are spending more time online since the beginning of the pandemic. Even Facebook reported a 70% rise in time spent on its apps since the outbreak and a 50% increase in messaging apps.





















