
Three British private equity firms were duped into making bank transfers worth £1.1 million (around US$1.3 million) following a sophisticated Business Email Compromise (BEC) attack, according to Check Point’s newly released threat report. Check Point’s Incident Response Team (CPIRT) discovered a hacker group dubbed “The Florentine Banker,” which targeted three unnamed firms for several months via phishing attacks, using fake emails and look-alike domains.
It is said that hackers made four separate bank transactions, in December 2019, to transfer £1.1 million to fraudulent bank accounts in Hong Kong and the U.K. An emergency intervention allowed banks to salvage £570,000 (US$702,067), the rest of the money lost permanently.
The Florentine Banker group targeted senior executives and those in charge of money transactions, including CEOs and CFOs via phishing attacks.
What is a BEC Attack?
A BEC attack is a sophisticated scam targeting an end-user or a business entity that performs electronic payments like wire transfers or automated clearing house transfers. In a BEC attack, the attackers first steal legitimate business email account credentials, which are later used to launch financial fraud campaigns like fraudulent email messages, requests for out-of-channel funds transfers, and deleted accounting trails.
How is the Attack Initiated?
Hackers try to lure the target into clicking on a link that lets them download malware onto their devices or trick into entering usernames and passwords that allow the attacker to steal credentials. Once the hackers gain control over the officials’ emails, they continue the attacks for weeks to gain control of other email accounts and carry out reconnaissance to understand the financial picture of the companies.
Phishing email sent by the Florentine Banker group
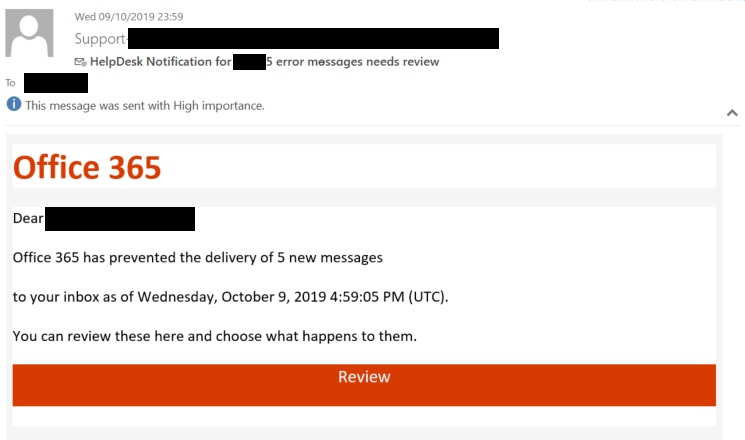
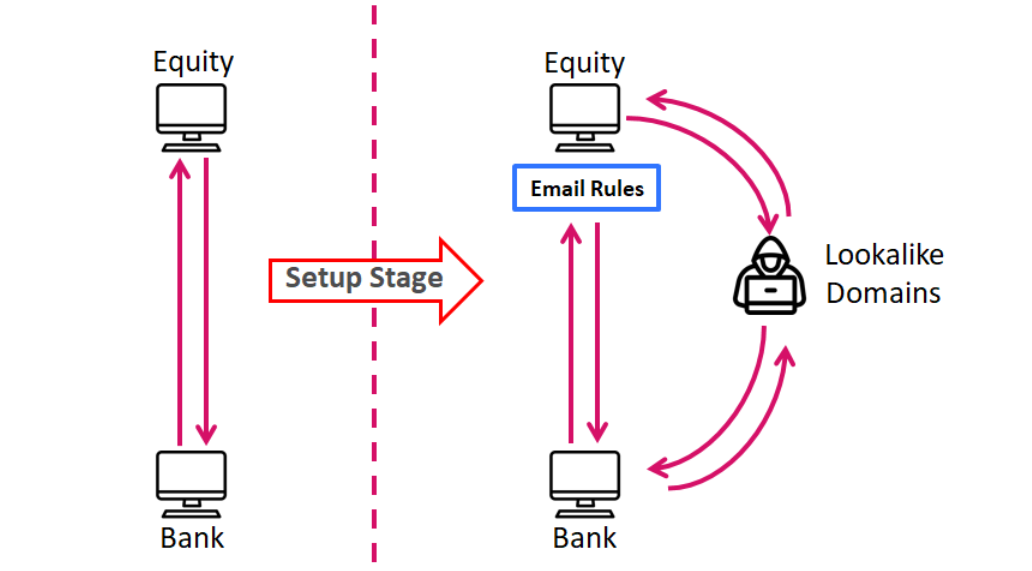
The hackers create mailbox rules to divert emails related to the theft to special inboxes monitored by the hacker group. This is done via Man-in-the-Middle (MITM) attack. Apart from infiltrating email accounts, the hackers also register lookalike domains that mimic the original ones of the targeted entities. Hackers then launch a MITM attack by sending emails from the fraudulent domains on behalf of the original enterprises.
With this set-up, the hackers inject fraudulent bank account information (associated with accounts located in Hong Kong and the U.K.) in the emails to divert money transfers and initiate new transfer requests.
Email Flow Before and After the Setup
“The Florentine Banker manipulates the conversation until the third-party approves the new banking details and confirms the transaction. If the bank rejects the transaction due to a mismatch in the account currency, beneficiary name or any other reason, the attackers are there to fix the rejects until the money is in their own hands,” Check Point added.
FBI Warns About Rising BEC Attacks
Recently, the FBI warned that organizations that use cloud-based email systems are at high risk to BEC attacks. The bureau advised employees about the email scams that begin with phishing kits designed to mimic two popular cloud-based email services to lure employees into compromising business email accounts and misdirecting funds transfers. The FBI stated that its Internet Crime Complaint Center (IC3) received complaints, between January 2014 and October 2019, claiming more than US$2.1 billion losses from BEC scams.





















