
By Safe-T
Safe-T provides a secure application and file access solution with 1) An architecture that implements Zero Trust Access, 2) A proprietary secure channel that enables users to remotely access shared sensitive files, and 3) User behavior analytics.
Safe-T’s package of access control software is called: Safe-T Zero+. Best practices guidelines require organizations to implement a phased deployment. This enables your organization to progressively migrate to a Zero Trust network architecture.
By implementing Safe-T’s Zero+ in steps you gain these advantages:
- Your organization learns to use the new system gradually.
- Information acquired from early deployment stages can be applied to the rest of the process.
- Your organization lowers its risks because any issue that might occur only affects a small group of users.
- IT administrative implementation burden is limited.
- Software evaluation trial period cost is limited.
Overview: Network Security Challenges
This section describes the contextual background of existing IT problems Safe-T’s Zero+ model can solve.
Security Perimeter: Most data centers implement a security perimeter model that establishes zones of trust based on ranges of IP addresses. They deploy back-to-back firewalls creating a DMZ that separates their trusted internal network from the external untrusted internet.
This type of fixed perimeter no longer accurately reflects the typical topology of users and servers.
Trusted Zones: A hacker who infiltrates the inner firewall of an organization is inside what is regarded as a trusted area. The hacker can then move about laterally stealing credentials and using them to capture and exfiltrate valuable digital resources.
Cloud Applications: Companies are increasingly deploying web applications and data on public clouds such as Amazon Web Services and Microsoft Azure. These public clouds are located in geographical locations remote from an organization’s trusted firewalls and perimeter network.
Mobile Workers: Company networks are expanding in size and complexity. Employees, contractors, and partners use laptops and other mobile devices offsite in locations external to the trusted perimeter network.
VPNs: Using VPNs to access an internal network can create a vulnerability if an administrator grants overly broad permissions to users. VPNs are often configured enabling users to access the inner network as if the user was onsite in a company office.
Malware: A serious problem with the use of VPNs is they create a high level of risk that malware in a user’s device can spread to an inner network.
What Is Zero Trust Network Access
These are key principles of a Zero Trust network:
Trust Nothing: Users and network traffic are not trusted until verified. Users whether inside or outside the organization’s network should never be trusted by default.
Visibility: Backend servers are not visible to unauthenticated users.
Authentication: Authentication workflows for a user or group should include context-aware data such as device ID, geographic location, and the time and day the user requests access.
Granularity: Zero trust supports network micro-segmentation isolating IT resources to limit threats. It also implements a policy of least privilege by enforcing controls that enable users to have access only to resources needed to perform their jobs.
Logs: All traffic internally as well as externally is logged to detect malicious or anomalous events.
Main Components
The Cloud Security Alliance is the leading proponent of SDP standards and research. The CSA working group on SDP has devised a security framework that can be deployed to protect applications from network-based attacks.
SDP architectures offered by different vendors may support different characteristics. Safe-T’s SDP architecture is designed to substantially implement the essential capabilities delineated by the CSA architecture. Safe-T’s Zero+ is built using these main components:
Safe-T Access Controller
The Access Controller is the SDP system’s centralized control and policy enforcement engine. The Access Controller is designed to function as a trust broker by governing the process flow between end users and backend services. The Access Controller has the responsibility for managing end user authentication and authorization.
Safe-T Access Gateway
The Access Gateway acts as a front-end to all backend services published to an untrusted network (e.g. Internet).
Safe-T Authentication Gateway
The authentication gateway presents to the end user in a clientless web browser a pre-configured authentication workflow provided by the Access Controller. The authentication workflow is a customizable set of authentication steps such as: captcha, user name/password, No-Post, OTP.
If the user successfully authenticates, the Authentication Gateway displays links enabling the user to connect to authorized backend services.
Unauthorized backend services are not visible to the end user. As stated by Safe-T: If you can’t be seen, you can’t be hacked®.
Safe-T’s Software Perimeter
The following image shows the basic Safe-T SDP architecture.
Safe-T Software Defined Perimeter
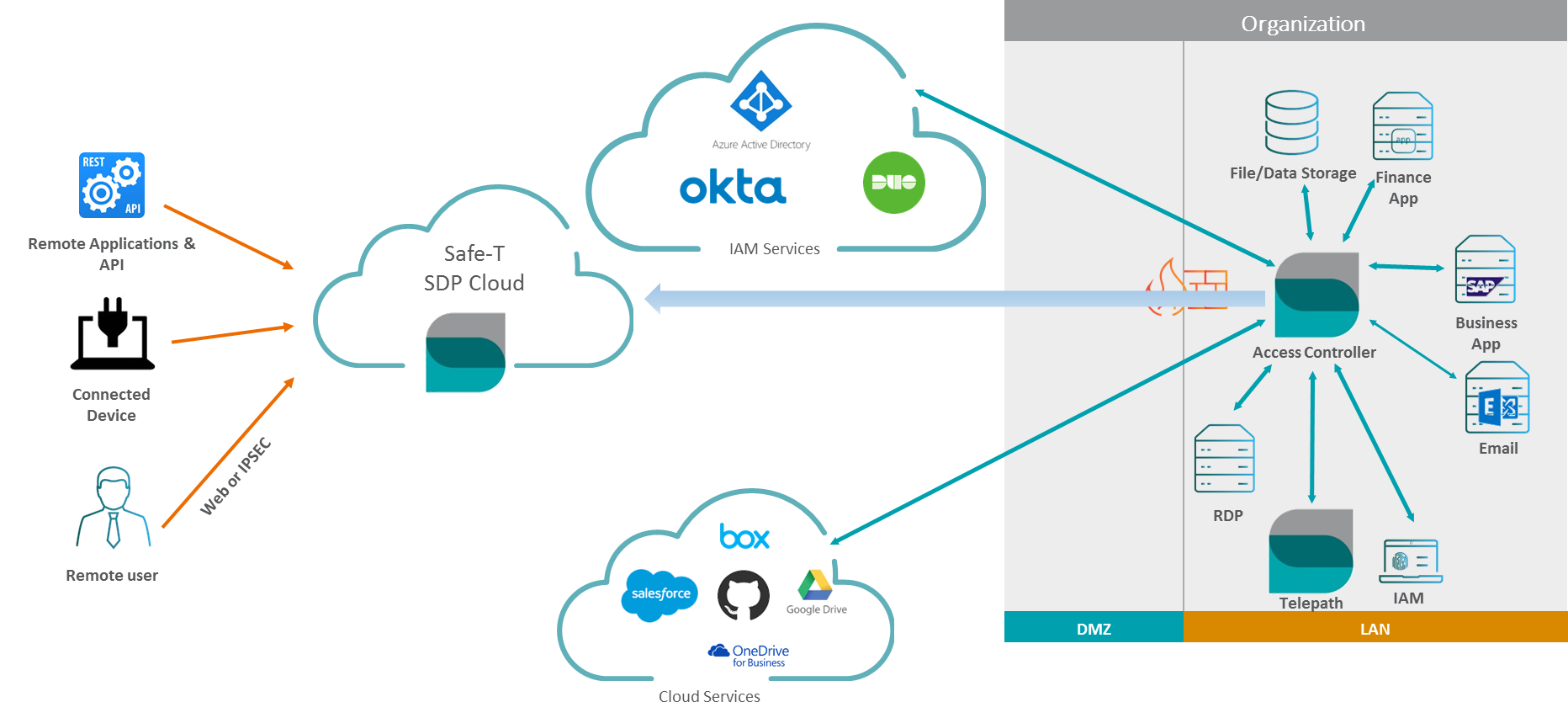
Safe-T Zero+ Capabilities
- Users who want to access a protected server must successfully authenticate and be authorized at an authentication gateway.
- Configurable policies define orchestrated authentication steps each user or group member is required to perform.
- Backend servers are not visible to unauthenticated users. The probability of successful attacks is minimized following Safe-T’s axiom: If you can’t be seen, you can’t be hacked®.
- Eliminates the possibility of users establishing a direct connection from an untrusted network to specific hosts in the internal Provides URL rewriting to hide backend services.
- Implements a patented technology to eliminate the need to open incoming ports in the internal firewall. Eliminates the need to store sensitive data in the DMZ.
- Support a variety of communication protocols: HTTP/S, SMTP, SFTP, APIs, RDP, WebDAV.
- Extends to on-premises, public, and hybrid cloud. Zero+ can be deployed on AWS, Azure, and other cloud infrastructures protecting both cloud and on-prem resources.
- Provides user behavior analytics capability that monitors the actions of protected web applications. A dashboard displays security related events and aggregated statistics. Administrators work at the dashboard to inspect details about anomalous behavior that can trigger alerts and identify suspicious activities.
- Provides a unique, native HTTPS-based file access solution for NTFS file system, replacing the vulnerable SMB protocol. Users can create a standard mapped network drive in their Windows explorer providing a secure, encrypted, and access-controlled channel to shared backend resources.
Types Of SDP Architectures
Customers can select an SDP architecture that meets their on-prem or cloud-based requirements:
- The customer deploys three VMs: 1) Access Controller, 2) Access Gateway, and 3) Authentication Gateway. The VMs can be deployed on-premises in an organization’s LAN, on Amazon Web Services (AWS) public cloud, or on Microsoft’s Azure public cloud.
- The customer deploys the 1) Access Controller VM and 2) Access Gateway VM on-premises in their LAN. The customer deploys the Authentication Gateway VM on a public cloud such as AWS or Azure.
- The customer deploys the Access Controller VM on-premises in their LAN and Safe-T deploys and maintains two VMs 1) Access Gateway and 2) Authentication Gateway both hosted on Safe-T’s private global cloud.
Info: The third SDP architecture option described above implements a hybrid SaaS model with shared deployment responsibilities. Safe-T deploys and manages two of the SDP VMs in the Safe-T private global cloud and the customer deploys one node the Access Controller VM on their premises.
How To Configure Phased Deployment
This section describes the basic steps for a limited SDP deployment involving a small number of users (e.g. 20) and backend servers (e.g. 5). Best practices are outlined below but your organization may deploy Safe-T Zero+ according to your site requirements.
Note: It is assumed you have selected the SDP architecture you want to deploy.
Phased Deployment of Backend Services
Select a small number of backend servers that contain low sensitive data. For example, choose a server used primarily by experienced users such as DevOps or QA personnel. This ensures risk is minimal if any problem occurs during the phased deployment of SDP access in your organization.
In the Access Controller web interface you must configure a reverse access rule for each backend server. The example below shows two reverse access rules: 1) a rule to connect to the Safe-T Authentication Gateway, and 2) a rule to connect a backend github server.
Figure 1: Safe-T Reverse Access Rules For Phased Deployment
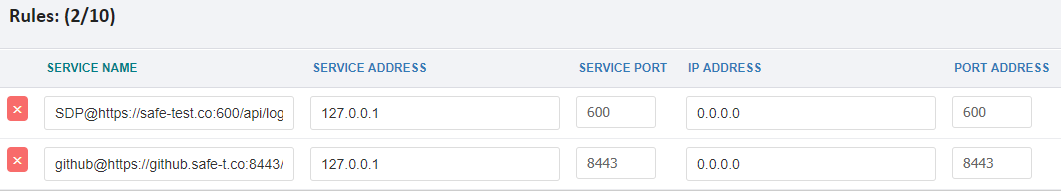
Phased Deployment Of User Groups
The Safe-T Access Controller provides a configuration feature called: Trusted Services. Using the admin web interface you can connect one or multiple groups to one or multiple backend services.
Example: To configure an organization’s AD server as a trusted service you could configure the following:
- Group name: Sales;Marketing
- Service name: AD
Replacing Your VPNs With SDP
The following list describes some problems that may be experienced by an organization using VPNs for remote access:
- Grants all-or-none access to the assigned network.
- Does not offer different levels of access for different users.
- Cannot easily adjust to dynamic changes in your network.
- Generates administrative complexity and cannot easily handle cloud or multiple network environments.
- Secures remote users but not users who are on-prem.
- Follows a site-centric model instead of user-centric.
- Requires installation of end-user VPN software clients.
Info: According to Gartner consultants, by 2021, 60% of enterprises will phase out network VPNs for digital business communications in favor of software-defined perimeters.
Safe-T suggests the following paths for phasing in SDP as a VPN replacement or for using VPNs and SDP in parallel.
Using VPNs and SDP In Parallel
This deployment solution implements a parallel VPN and SDP architecture. You start the migration by selecting a group of VPN users (e.g. Partners). Ask these users to log into the SDP Authentication Gateway web UI instead of using their VPN client.
Evaluate SDP access and when the advantages of using SDP are demonstrated to the satisfaction of your IT department remove the VPNs from that group of SDP users. Continue reducing the number of VPN users while simultaneously granting them SDP access.
Using VPNs As The Front End For SDP Access
This strategy uses your organization’s existing VPN framework as a front end for accessing the SDP Authentication Gateway.
The process flow is as follows:
- A user opens their SSL or IPsec VPN client and logs into the VPN gateway.
- The VPN gateway transfers the user’s credentials over a RADIUS connection to the SDP Authentication Gateway.
- The Access Controller retrieves the credentials from the Authentication Gateway over a reverse access connection and authenticates the user with a third-party IAM/IDP solution such as Microsoft Azure AD.
- If the user is authenticated, the Access Controller sends a RADIUS response via the Authentication Gateway to the VPN client indicating the user is authenticated.
- The Access Controller instructs the Access Gateway to provide reverse access to the user’s virtual IP address that is provided by the VPN gateway.
- The user can access the authorized services.
Info: The above deployment architecture can be used as a migration path to SDP-only access if your organization chooses to phase out using their SSL or IPsec VPN
Note: If you use VPNs as a front end for SDP access the end user does not log into the SDP Authentication Gateway.
SDP Market Trends
A recent survey by the Cloud Security Alliance indicates SDP awareness and adoption is still in its early stage of growth. This is an excerpt from the CSA Survey:
The State of SDP Survey: A Summary, Cloud Security Alliance, July 2, 2019
https://blog.cloudsecurityalliance.org/2019/07/02/the-state-of-sdp-survey-a-summary/
“The survey indicates it is still early for SDP market adoption and awareness, with only 24% of respondents claiming that they are very familiar or have fairly in-depth knowledge of SDP. The majority of respondents are less knowledgeable, with 29% being “somewhat” conversant in SDP, 35% having heard of it, and 11% knowing nothing about it.”
“A majority of organizations recognize the need to change their approach to a Zero Trust Architecture– 70% of respondents noted that they have a high or medium need to change their approach to user access control by better securing user authentication and authorization.”
Conclusion
Safe-T’s Zero+ network access can help manage and improve an organization’s network security.
Organizations want to protect their applications and data whether on-prem, hybrid, or in a public cloud. They also want to secure network access for users who are working in any geographic location.
IT professionals across a wide range of industries are learning about the advantages of a Zero Trust access network.
CISO MAG does not evaluate the advertised product, service, or company, nor any of the claims made by the advertisement. The facts, opinions, and language in the article do not reflect the views of CISO MAG and CISO MAG does not assume any responsibility or liability for the same.





















